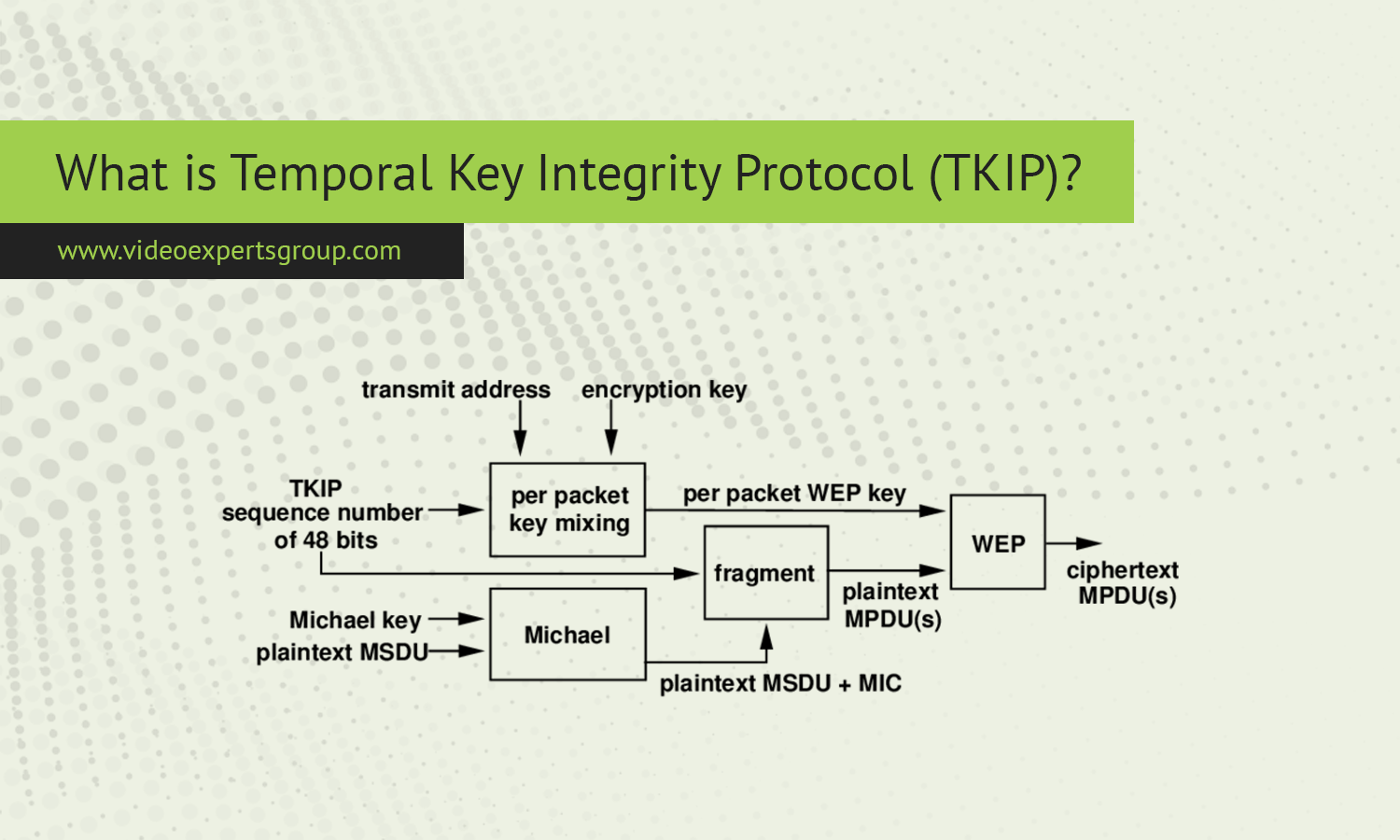
In the realm of wireless networks, ensuring secure communication is critical to protect data from unauthorized access and malicious attacks. One of the protocols that played a significant role in enhancing Wi-Fi security was the Temporal Key Integrity Protocol (TKIP). TKIP was introduced as part of the Wi-Fi Protected Access (WPA) security standard and was primarily designed to address vulnerabilities in the earlier WEP (Wired Equivalent Privacy) protocol. Although it is now considered outdated and less secure than modern encryption protocols like AES, TKIP was once a vital step in securing wireless communication.
Meaning
Temporal Key Integrity Protocol (TKIP) is an encryption protocol used in wireless networks to enhance data security. It was introduced as a part of the WPA (Wi-Fi Protected Access) standard to address the weaknesses in the older WEP (Wired Equivalent Privacy) encryption. TKIP uses dynamic key generation to secure wireless traffic, meaning that it changes encryption keys frequently, making it harder for attackers to decrypt wireless traffic. TKIP was designed to be backward-compatible with older WEP hardware, allowing users to upgrade their network security without replacing existing equipment.
What is TKIP used for?
TKIP was primarily used in wireless networks to secure communication between devices and prevent unauthorized access to data transmitted over Wi-Fi. Its key features, such as dynamic key generation and per-packet key mixing, were developed to fix the security flaws in WEP, which relied on static encryption keys that could easily be cracked by attackers.
TKIP was introduced as a temporary solution during the transition from WEP to more advanced security protocols like WPA2, which uses AES (Advanced Encryption Standard) for stronger encryption. Although TKIP is now largely obsolete, it was widely used in wireless networks during the early 2000s to improve Wi-Fi security in environments where upgrading to WPA2 or new hardware was not immediately feasible.
How does TKIP work?
TKIP enhances the security of wireless networks in several ways:
-
Per-Packet Key Mixing: TKIP generates a new key for each data packet sent over the network. This dynamic key mixing prevents attackers from using known encryption attacks, such as replay attacks, where the same key is repeatedly reused.
-
Message Integrity Check (MIC): TKIP includes a mechanism to ensure data integrity by detecting if a packet has been altered during transmission. This helps protect the network from man-in-the-middle attacks or packet tampering.
-
Rekeying Mechanism: Unlike WEP, which uses static keys, TKIP rekeys every few minutes. This dynamic key generation makes it significantly harder for attackers to intercept and decrypt wireless traffic.
-
Backward Compatibility: One of TKIP’s design goals was to work with older WEP-compatible devices. It allowed legacy hardware to upgrade security without requiring new equipment, which was especially beneficial during the WPA transition.
TKIP Vulnerabilities
Although TKIP improved upon WEP, it is no longer considered secure by modern standards due to several vulnerabilities:
-
Susceptibility to Attack: TKIP still has several weaknesses that can be exploited by attackers. For instance, certain attacks, like the "Beck-Tews" attack, can decrypt small amounts of data by exploiting flaws in TKIP’s MIC function.
-
Replay Attacks: Even though TKIP employs per-packet key mixing, it is still vulnerable to replay attacks under certain circumstances, where attackers can intercept and retransmit data packets to cause network disruptions.
-
Obsolescence: TKIP was designed as a stopgap measure, and with the introduction of WPA2, which uses AES encryption, TKIP became outdated. AES provides far stronger encryption and security features, rendering TKIP obsolete in modern wireless networks.
For these reasons, the Wi-Fi Alliance deprecated TKIP, and most modern routers and devices do not support it for new installations. WPA2 (AES) or WPA3 should be used instead.
Advantages and Disadvantages of TKIP
Advantages:
-
Backward Compatibility: TKIP was designed to work with legacy WEP hardware, allowing users to enhance network security without replacing older equipment.
-
Improved Security Over WEP: TKIP fixed many of the vulnerabilities in WEP, such as the use of static keys, by introducing dynamic key generation and per-packet key mixing.
-
Dynamic Key Management: TKIP’s ability to change keys frequently made it harder for attackers to intercept and decrypt wireless data compared to WEP.
Disadvantages:
-
Vulnerabilities: TKIP is still vulnerable to certain types of attacks, including replay and packet injection attacks, making it less secure compared to modern protocols like AES.
-
Performance Impact: The additional processing required for key generation and integrity checks can slightly reduce the performance of the network, especially in older devices.
-
Obsolescence: TKIP is no longer considered secure and has been deprecated in favor of stronger encryption standards like WPA2 (AES) and WPA3.
FAQ