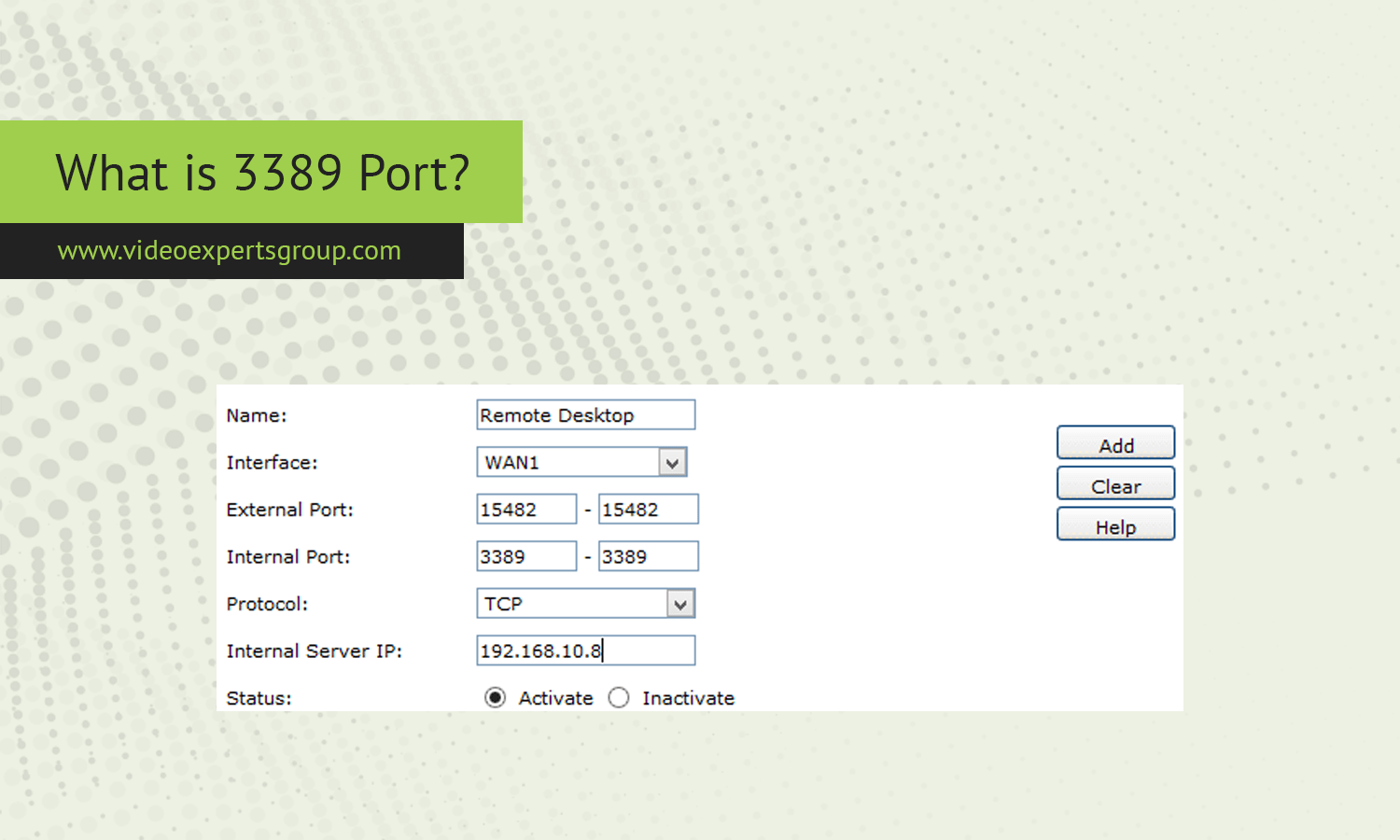
Port 3389 is well-known and widely used, especially in environments where remote access to computers is crucial. Whether you're managing a network, setting up remote work capabilities, or simply curious about how remote desktop connections work, understanding Port 3389 is key.
Meaning
Port 3389 is a specific port number assigned to the Remote Desktop Protocol (RDP). RDP is a proprietary protocol developed by Microsoft that allows users to connect to and control a remote computer as if they were sitting right in front of it. This port acts as the gateway through which RDP communications travel, making it possible for users to access their desktops, servers, and other devices from virtually anywhere.
RDP uses TCP and UDP on Port 3389 to establish a connection between the client (the device you’re using to connect) and the remote server or computer. This port number is the standard setting for RDP, and it's recognized across different systems and networks, allowing seamless remote access.
What is Port 3389 Used For?
Port 3389 is primarily used for remote desktop connections. Here’s how it functions in different scenarios:
-
Remote Desktop Services (RDS): Port 3389 is the default port for Microsoft’s Remote Desktop Services, which allows multiple users to connect to a central server and access applications, desktops, and data remotely. This is particularly useful in corporate environments where centralized management and resource sharing are important.
-
Remote Assistance: IT support teams often use RDP over Port 3389 to provide remote assistance to users experiencing technical issues. By connecting to a user’s machine remotely, technicians can troubleshoot problems, install software, and configure settings without needing to be physically present.
-
Virtual Desktop Infrastructure (VDI): In VDI setups, where virtual desktops are hosted on servers, Port 3389 is used to deliver the virtual desktop experience to end-users. This allows users to access a consistent desktop environment from various devices.
-
Accessing Home or Office PCs: Many people use RDP to access their home or office computers from a different location, such as when working remotely or traveling. By using Port 3389, they can access files, run applications, and manage their systems from afar.
Vulnerabilities
While Port 3389 is incredibly useful, it’s also a common target for cyberattacks due to its widespread use and the fact that it provides direct access to systems. Here are some of the vulnerabilities associated with Port 3389:
-
Brute-Force Attacks: Since RDP over Port 3389 is often exposed to the internet, attackers can use brute-force methods to guess usernames and passwords. If strong authentication methods are not in place, this can lead to unauthorized access.
-
RDP Exploits: Over the years, several vulnerabilities have been discovered in the RDP protocol itself, such as the BlueKeep vulnerability (CVE-2019-0708). Exploits targeting these vulnerabilities can allow attackers to execute arbitrary code, potentially taking control of a system without needing valid login credentials.
-
Man-in-the-Middle Attacks: If the RDP session is not properly secured, attackers can intercept the communication between the client and the server, potentially capturing sensitive information such as passwords or session data.
-
Denial of Service (DoS) Attacks: Attackers can target Port 3389 with DoS attacks to overwhelm the service, causing legitimate users to be unable to connect. This can disrupt business operations, especially in environments heavily reliant on remote desktop services.
-
Weak Security Configurations: If RDP is not configured securely, such as using outdated encryption methods or not enabling Network Level Authentication (NLA), it can be easier for attackers to exploit vulnerabilities associated with Port 3389.
Port 3389 plays a vital role in enabling remote desktop connections, making it a cornerstone of modern network management and remote work setups. However, its widespread use also makes it a prime target for cyberattacks. Understanding the purpose of Port 3389 and the vulnerabilities associated with it is crucial for anyone responsible for securing networks or providing remote access. By implementing strong security measures, such as robust authentication, encryption, and limiting exposure to the internet, the risks associated with Port 3389 can be significantly mitigated.